Today we take a look at a pdf exploit malware (md5 is 1cf1128b9190d7344c200e1e944d7abf).
First of all let’s open the pdf file with a text editor and dig into it:
As we can see from the object definition, we have a stream compressed with zlib:

We can code a small python script that will do all the dirty work (decompress and make code readable) for us.
The following is our stream after decompression:
The above javascript code, retrieves the second stream located in the first page of the pdf file and handles this stream.
To locate the second stream, it uses the syncAnnotScan method in order to scan all the annotations in the document and then it uses getAnnots to retrieve the list of annotation and then picks up the first one, our second stream. For details about javascript/acrobat, please take a look here.
It decodes this stream by replacing (using a global replacement ‘z’ with ‘%’) with the regexp “/z/g,’%’” so it calls unescape and finally it calls eval.
Our uncompressed stream fixed is (click on the following images to enlarge):
Ok, let’s have fun with this joyful and clear javascript function 😦
The first parameter (FfVKaBvcfE3268e) is set to 0 and the second one (JJ140q) is obviously an encoded code string. As we can see, this function handles the encoded code string (full dump here) in order to deobfuscate the code itself. The code is another javascript, as we can see from the eval (eval(n__YJ78gI18RI)) call at the end of this second function.
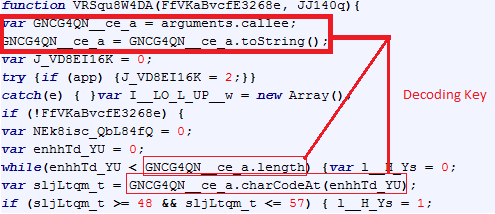
At the beginning of the function, we have an anti-debug trick:
This trick is discussed here. It uses its own javascript code (by using the arguments.callee) as the key to deobfuscate the code string discussed above.
If we take a closer look at this function, we can notice that the key is built only by using the number chars into this function code. Here is a small python script that extracts the key:
key = "" for i in range(0, len(data)): if data[i] >= '0' and data[i] <= '9': key += data[i] print key
Let’s look at the final functions (we just focus on the relevant parts).
First of all, the exploit is related to an old version of Adobe Reader as we can see in the following snippet:
Another interesting part is this function in which it handles the shellcode:
We can obtain the website which it connects to download the malware from the shellcode:
At this time this website seems to be offline, so no further analysis can be done on the downloaded malware.
The exploit used is related to an old vulnerability that is reported here.
Ok that’s all… see you next post 🙂





thx ratsoul, a very interesting reading ; )